TrustDevice-Android
A lightweight library for determining device uniqueness and risk identification.
Create a device identifier based on basic device information.
Will remain the same after uninstalling and reinstalling or clearing app data.
Quick start
1. Add repository
Add these lines to your build.gradle.
allprojects {
repositories {
maven { url 'https://jitpack.io' }
}
}
If your version of Gradle is 7 or newer, add these lines to your settings.gradle:
repositories {
...
maven { url 'https://jitpack.io' }
}
2. Add dependency
Add these lines to build.gradle of a module.
dependencies {
...
implementation 'com.github.trustdecision:trustdevice-android:1.0.1'
}
3. Get deviceInfo
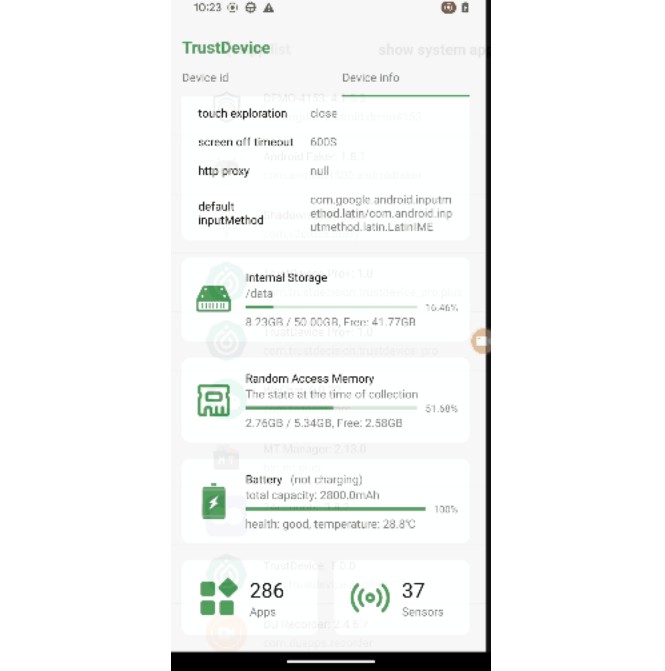
DeviceInfo contains device id, risk information and device details.
3.1. Option 1
// initialization
TDRisk.init(context);
// usage
JSONObject deviceInfo = TDRisk.getBlackbox();
// Obtain deviceid and risk information through deviceInfo
String deviceID = deviceInfo.optString("device_id");
JSONObject deviceRisk = deviceInfo.optJSONObject("device_risk_label");
JSONObject deviceDetail = deviceInfo.optJSONObject("device_detail");
getBlackbox method executes in the calling thread and takes time to execute.
3.1.2. Option 2
TDRisk.Builder builder = new TDRisk.Builder();
builder.callback(new TDRiskCallback() {
@Override
public void onEvent(JSONObject deviceInfo) {
// Obtain deviceid and risk information through deviceInfo
String deviceID = deviceInfo.optString("device_id");
JSONObject deviceRisk = deviceInfo.optJSONObject("device_risk_label");
JSONObject deviceDetail = deviceInfo.optJSONObject("device_detail");
}
});
TDRisk.initWithOptions(context, builder);
callback is in a sub-thread, please do not perform UI operations.
Data Sample
{
"device_id": "E9BE9A73B4AEA5A94B36FABC0BF5AF302DC332E4BCB7D10F5F5F7B507DF2A782",
"device_risk_label": {
"root": "false",
"debug": "true",
"multiple": "false"
},
"device_detail": {
"abiType": "arm64-v8a,armeabi-v7a,armeabi",
"accessibilityEnabled": "0",
"adbEnabled": "1",
"allowMockLocation": "0",
"androidId": "5fa5f2bdc283000c",
"androidVersion": "13",
"appList": "com.trustdevice.android",
"availableMemory": "2981945344",
"availableStorage": "50888110080",
"batteryHealthStatus": "good",
"batteryLevel": "76",
"batteryStatus": "charging",
"batteryTemp": "230",
"batteryTotalCapacity": "2800.0",
"brand": "google",
"coresCount": "8",
"country": "CN",
"cpuHardware": "Qualcomm Technologies, Inc SM8150",
"cpuProcessor": "AArch64 Processor rev 14 (aarch64)",
"dataRoaming": "0",
"debug": "true",
"defaultInputMethod": "com.google.android.inputmethod.latin/com.android.inputmethod.latin.LatinIME",
"developmentSettingEnabled": "1",
"display": "TP1A.220624.014",
"filesAbsolutePath": "/data/user/0/com.trustdevice.android/files",
"fingerprint": "google/flame/flame:13/TP1A.220624.014/8819323:user/release-keys",
"gsfId": "",
"hardware": "flame",
"host": "abfarm-release-rbe-64-00043",
"httpProxy": "null",
"kernelVersion": "4.14.276-g8ae7b4ca8564-ab8715030",
"language": "zh",
"manufacturer": "Google",
"mediaDrmId": "A069CC34B11C17F1C390575C794166F83CDE53B0887D2F718EDC901ED337FDF4",
"model": "Pixel 4",
"packageName": "com.trustdevice.android",
"product": "flame",
"root": "false",
"screenBrightness": "63",
"screenOffTimeout": "30000",
"screenResolution": "1080x2280",
"sdkVersion": "33",
"sensorsInfo": "LSM6DSR Accelerometer:STMicro,LIS2MDL Magnetometer:STMicro,LSM6DSR Gyroscope:STMicro,TMD3702V Ambient Light Sensor:AMS",
"systemAppList": "com.google.android.networkstack.tethering,com.google.omadm.trigger",
"timezone": "中国标准时间",
"totalMemory": "5730922496",
"totalStorage": "53684973568",
"touchExplorationEnabled": "0"
}
}
Open Source Features
- Basic device ID, This identifier is stable, it will remain the same even after uninstalling and reinstalling your app. But it will be different after factory reset of the device.
- Basic equipment information, which can be used for simple data analysis
- Basic risk identification ability
| RiskLabel | Risk Description |
|---|---|
| root | Attackers will have higher privileges and can install many cheating software to affect the normal development of application business. |
| debug | Applications can be modified by attackers at will, and the program will return unexpected values. |
| multiple | Attackers can clone multiple app. |
Open Source VS Pro
| Open Source | Pro | |
|---|---|---|
| 100% open source | Yes | No |
| Device ID | Basic | Extremely stable |
| Device Risk Label | Basic | Extremely rich |
| Device Details | Basic | Extremely rich |
| IP Location | – | ✓ |
| Device Risk Score | – | ✓ |
| Environment Risk Evaluation | – | ✓ |
| Fraud Tools Detection | – | ✓ |
| Behavioral Activity Capturing | – | ✓ |
Pro Introduction
TrustDecision TrustDevice has the leading device fingerprint technology, which has been integrated by more than 10000 global leading brands, protecting the entire customer journey.
There are 6 leading core features about TrustDevice Pro:
1. Wide Coverage
Comprehensive coverage of Android, iOS, Web, H5, applets and other device types.
2. Stable and Reliable
TrustDevice served more than 10,000 clients, 200 million+ daily active users , and 6 billion+ devices , with excellent product functions and stability. The fingerprint accuracy of different terminal devices exceeded 99.9%, and the output of risk labels exceeded 70 items.
3. Unparalleled Safety
TrustDevice’s code virtualization & obfuscation technology make the malware fraudsters suffer from painful cost and imprecision when performing reverse-engineering.
4. Core Intellectual Property
Fully independent intellectual property rights, with a number of patented technology.
5. Security Compliance
TrustDevice is committed to the highest standards in security and compliance to keep your data safe. GDPR/CCA/PCI DSS/ISO 27701/ISO 9001 Compliant.
6. Easy to Deplo
SaaS(Software as a Service)deployment supported, reducing massively your integration cost and enabling rapid access to device fingerprint service.
Where to get support
We are happy to provide technical support for our open-source trustdevice-android library. We recommend using GitHub Issues to submit bugs or Discussions to ask questions. Using Issues and Discussions publicly will help the open-source community and other users with similar issues.
In addition, any idea or interest in using TrustDevice Pro can be found on the www.trustdecision.com, registered account for a free trial; or via email trustdevice@trustdecision.com contact us directly and quickly open the service.
TrustDevice Android Demo App
Try the library features in the TrustDevice Android Demo App.
Compatibility
| Items | Description |
|---|---|
| Supported System Versions | Android5.0+ ( API 21+ ) |
| Supported Architecture | armeabi-v7a, arm64-v8a, x86 |
TrustDevice Pro VS Others
| Type | Scene | Result | TrusDevice Pro | Fingerprint | Seon | Sift |
|---|---|---|---|---|---|---|
| Device Fingerprint Compatibility | Support Hongmeng system, including HarmonyOS 3.0, etc. | Able to collect device info and generate device ID | ✅ | ✅ | ✅ | ✅ |
| Android 5.0 and above, including Android 14, etc. | Able to collect device info and generate device ID | ✅ | ✅ | ✅ | ✅ | |
| Device fingerprint uniqueness | Different Apps (with different package names) on the same device | Device fingerprint/ID matches | ✅ | ✅ | ✅ | ✅ |
| The same app on two unique devices (including the case of the same device model and the same system version) | Device fingerprint/ID should not match. Each device to have its own unique device fingeprint/ID | ✅ | ✅ | ✅ | ✅ | |
| Device Fingerprint Stability | Uninstall and reinstall of app | Device fingerprints/ID are consistent before and after reinstallation | ✅ | ✅ | ✅ | ✅ |
| Clear all app data | Device fingerprints/ID are consistent before and after clearing all app data | ✅ | ✅ | ✅ | ✅ | |
| Disable all app permissions except network permissions and clear app data | Device fingerprints/ID are consistent before and after disabling all permissions | ✅ | ✅ | ✅ | ✅ | |
| Modify the common information of the device system (brand, model, IMEI number, MAC address, etc.) through the device modification tool | Device fingerprint/ID still matches with before modification | ✅ | ✅ | ✅ | ❌ | |
| Running same app in two instances using virtualization on the same device (i.e. using parallel space or dual space tools) | Device fingerprint/ID still matches between both app instances | ✅ | ✅ | ✅ | ✅ | |
| Android system upgrade | Device fingerprint/ID are consistent before and after system upgrade | ✅ | ✅ | ✅ | ✅ | |
| Factory reset (including Android 10 and above, etc.) | The device fingerprints are the same before and after the device is restored to factory settings | ✅ | ❌ | ❌ | ❌ | |
| Device Fingerprint Risk Identification | Secondary packaging | Ability to identify secondary packaged unofficial apps | ✅ | ❌ | ❌ | ❌ |
| Replay attack | Ability to identify replay attacks | ✅ | ❌ | ❌ | ❌ | |
| Suspected risky ROM | Ability to identify suspected risky ROMs | ✅ | ❌ | ❌ | ❌ | |
| Device location information has been tampered with | Ability to identify tampering of location information | ✅ | ❌ | ❌ | ❌ | |
| The device does not have a SIM card inserted | Can identify whether the device is inserted with a SIM card | ✅ | ❌ | ❌ | ❌ | |
| The device uses an HTTP proxy | Can identify HTTP proxy risks | ✅ | ❌ | ❌ | ❌ | |
| The device uses a VPN proxy | Can identify VPN proxy risks | ✅ | ❌ | ❌ | ❌ | |
| The device is Rooted | Ability to identify root risks | ✅ | ❌ | ✅ | ✅ | |
| The device is an Android emulator | Can recognize emulator/simulator | ✅ | ❌ | ✅ | ❌ | |
| The device is an Android cloud emulator | Ability to recognize cloud emulators | ✅ | ❌ | ✅ | ❌ | |
| The device is an Android cloud real device | Can identify cloud real device | ✅ | ❌ | ❌ | ❌ | |
| Devices use system virtualization tools (i.e. parallel space, dual space, etc) | Able to identify system virtualization tools | ✅ | ❌ | ❌ | ❌ | |
| The device uses the virtualization tool to launch multiple instances of same application | Recognize multiple instances of same applications on same device opened via virtualization tool | ✅ | ❌ | ❌ | ❌ | |
| The device uses the device modification tool to modify the device parameter information | Ability to identify mainstream modification tools | ✅ | ❌ | ❌ | ❌ | |
| The device uses scripting tools | Can identify mainstream scripting tools | ✅ | ❌ | ❌ | ❌ | |
| The device uses the group control tool (tools to control multiple devices via a single terminal – device farm/device group) | Can identify mainstream group control tools | ✅ | ❌ | ❌ | ❌ | |
| The device is in Android ADB debugging state | Able to recognize Android ADB debugging | ✅ | ❌ | ❌ | ✅ | |
| The device uses offerwall software (ad scamming software) | Ability to identify devices using offerwall software | ✅ | ❌ | ❌ | ❌ | |
| Security and Stability | Code Protection | The device fingerprint SDK and JS have code protection mechanisms (such as VMP), which effectively resist black hat cracking attempts to manipulate code logic and falsify data | ✅ (OLLVM, VMP) | ❌ | ❌ | ❌ |
| Downgrade | Intercepting and sending collection requests in the Android environment can still generate device fingerprints normally | ✅ | ❌ | ✅ | ❌ | |
| Anti packet capture | Android has the ability to prevent packet capture | ✅ | ❌ | ❌ | ❌ |
License
This library is MIT licensed. Copyright trustdecision, Inc. 2022.